This demonstration is intended solely for educational use on systems owned by the reader or where explicit authorization has been granted. Unauthorized access is illegal and unethical.
The Architectural Weakness: Recovery Environment
The vulnerability stems not from the Windows lock screen mechanism, but from the Windows Recovery Environment (WinRE), a pre-boot diagnostic and repair system accessible through the Shift + Restart sequence.
WinRE was designed with legitimate system recovery in mind. To fulfill its diagnostic functions, it requires extensive access to system files and directories. The critical oversight lies in WinRE's trust model: on unencrypted systems, it assumes that anyone capable of initiating the recovery environment has legitimate administrative intent.
Phase 1: Recovery Environment Access
From the lock screen, execute Shift + Restart to boot into the Windows Recovery Environment (WinRE). When presented with the "Choose an option" screen, navigate to:
Troubleshoot → Advanced Options → Command Prompt
Phase 2: Binary Substitution
Osk.exe is the Windows executable for On-Screen Keyboard, an accessibility utility that displays a virtual keyboard on the screen so text can be entered without a physical keyboard using a mouse, touch, or other pointing device. This feature is visible from the accessibility menu provided before logging into the windows system. Note that any other binary present in the accessibility menu can be replaced.
The command prompt runs outside the normal Windows login context, providing elevated file system access on the installed drive, usually mounted as D: or E:. The elevated access in this mode sets the stage for the next step in the bypass process. Navigate to D:\Windows\System32 and run the following commands:
Backing up the content of osk.exe so that it does not get lost into the void.
copy osk.exe osk.exe.bak
Replacing the content of osk.exe with cmd.exe
copy cmd.exe osk.exe
Phase 3: Privilege Escalation
Upon rebooting, the Windows lock screen appears as usual, but when the Accessibility icon is clicked and "On-Screen Keyboard" is selected, the system instead opens a Command Prompt running under the NT AUTHORITY\SYSTEM account.
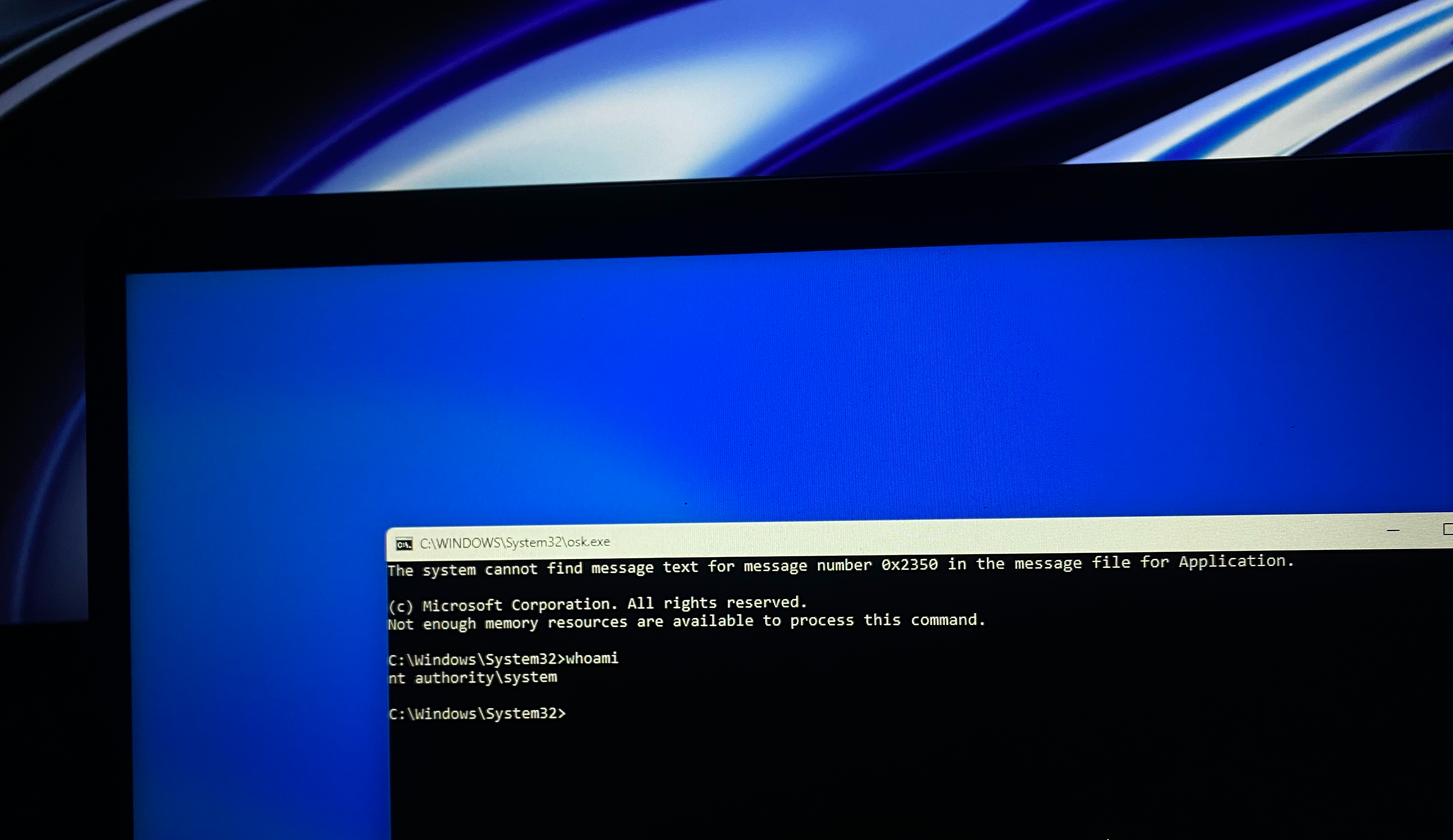
When you hold the highest Windows privilege level (NT Authority\System), the system becomes your playground. This shell allows executing commands to create new administrator accounts, reset existing passwords, or perform other administrative actions, effectively bypassing the usual login credentials.
Creating a new user account:
net user [username] [password] /add
Granting administrative privileges:
net localgroup administrators [username] /add
Resetting passwords for existing accounts:
net user <username> <new password>
Windows Home editions lack BitLocker entirely, and even among Windows Pro or Enterprise users, BitLocker is often not enabled. This leaves a substantial number of machines vulnerable, especially in environments where physical security cannot be guaranteed.
Credit: Pradeep Bhattarai